How to Check Which Block Cipher Modes of Operation Used
We will look at some of these here. HMAC was approved in 2002 as FIPS 198 The Keyed-Hash Message Authentication Code HMAC CMAC was released in 2005 under SP800-38B Recommendation for Block Cipher Modes of Operation.
Block Cipher Modes Of Operation Learn 5 Important Modes Of Operations
Cipher Feedback CFB Encryption parallelizable.

. Block cipher mode of operation. Used with an underlying block cipher algorithm that is approved in a Federal Information Processing. A mode of operation describes how to repeatedly apply a ciphers single-block operation to securely transform amounts of data larger than a block.
Block size n is predetermine by the underlying cipher. Cipher Block Chaining Mode. The CMAC Mode for Authentication and GMAC was formalized in 2007 under SP800-38D Recommendation for Block Cipher Modes of Operation.
In electronic codebook mode ECB the plain text is divided into the blocks each of 64-bit. A block cipher by itself is only suitable for the secure cryptographic transformation encryption or decryption of one fixed-length group of bits called a block. Most symmetric-key algorithms currently in use are block ciphers.
Each block is encrypted one at a time to produce the cipher block. In the CTR mode the final portion of the input data can be shorter then the. For example to encrypt and decrypt 8-bit characters.
Often used in authentication. For example for DES n 64 for AES n 128 In some situations we need use DES or AES as secure cipher but the plain text or cipher text block size are to be smaller. ECB Electronic Code Book mode.
Modes of Operations. Cipher FeedBack CFB 1. The size of each block is.
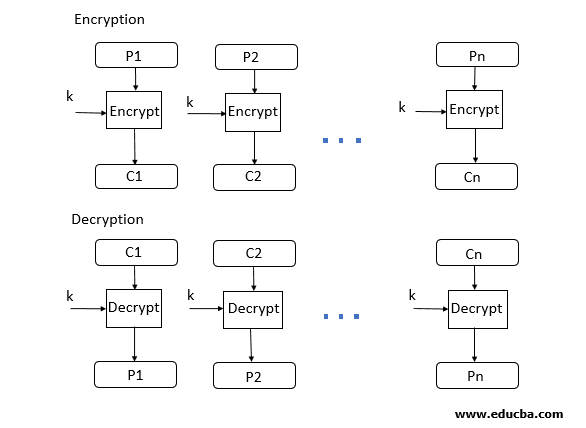
Block cipher works on a fixed-length group of bytes called a block. This means that they encrypt data a block at a time. This is considered to be the easiest block cipher mode of operation.
In cryptography a block cipher mode of operation is an algorithm that uses a block cipher to provide an information service such as confidentiality or authenticity. The cipher feedback CFB mode. When encrypting multiple blocks of data using a block cipher there are various encryption modes that may be employed each having particular advantages and disadvantages.
Converts block cipher into stream cipher No need to pad message to integral number of blocks Operate in real-time. The IV has to be non-repeating and for some modes random as well. To operate on longer texts than the block size we need to use a block cipher mode of operation.
Whether it is DES or AES. IV is first encrypted using the key and then XORed with the plaintext to create the ciphertext. DES would be the box in your diagram thats labeled Block Cipher Encryption and it participates in the encryption mode you show in two ways.
For each block in CTR mode a new unpredictable keystream block is generated based on the initial vector IV sometimes called nonce the current counter 01 02 03 the secret encryption key and the input block is merged by XOR with the current keystream block to produce the output block. Each character encrypted and transmitted immediately. Ct0 block_cipher_encryptXORpt0 IV key for i from 1 to lenpt.
The counter CTR mode. Electronic Codebook ECB worst. Cipher Block Chaining CBC widely used.
Most of Symmetric Cryptography Algorithms implemented in Intel IPP are Block Ciphers which operate on data blocks of the fixed size. Later in 2001 NIST the US National Institute of Standards and Technology added the following mode of operation for AES. The size of the data blocks depends on the specific algorithm.
The size of the key K used in a mode of operation depends on the used block cipher ie. The output is XORed with the plaintext and the output is used as the input to the next blocks use of DES the second Block Cipher Encryption. Ideally it should be random unpredictable and single-use.
Block Cipher Modes of Operation. Often used in authentication. About Press Copyright Contact us Creators Advertise Developers Terms Privacy Policy Safety How YouTube works Test new features Press Copyright Contact us Creators.
Cipher feedback mode ECB and CBC modes encrypt and decrypt blocks of the message. This recommendation defines five confidentiality modes of operation for use with an underlying symmetric key block cipher algorithm. A block cipher mode of operation usually just called a mode in context specifies how a block cipher should be used to encrypt or decrypt messages that are longer than the block size.
Figure 115 and Figure 116 show the Cipher Feedback mode CFB mode of operation applied for encryption and decryption respectively. It means that by using an only block cipher we would not be able to operate on longer plain text. Cti block_cipher_encryptXORpti cti-1 key For the other modes just look at Wikipedias article on modes of operation.
Electronic Codebook ECB Cipher Block Chaining CBC Cipher Feedback CFB Output Feedback OFB and Counter CTR. The ciphertext from the first step is XORed with the second plaintext block and the ensuing ciphertext is chained to the third step where it is encrypted. It usually does not need to be secret though it cannot be re-used.
The table below shows. This means that in practice we would not be able to encrypt for example our disk. The output feedback OFB mode.
It is not recommended however it is possible while working with block ciphers to use the same secret key bits for encrypting the same plaintext parts. Its a data block used by several modes of block ciphers to randomize encryption so that different cipher text is created even if the same plain text is repeatedly encrypted. The modes of operation of block ciphers are configuration methods that allow those ciphers to work with large data streams without the risk of compromising the provided security.
114 Cipher Feedback Mode. A mode of operation describes how to repeatedly apply a. Block Ciphers encrypt a plaintext block into a ciphertext block or decrypts a ciphertext block into a plaintext block.
For CBC mode you also need an IV but it is still pretty simple. In this mode youre using DES to generate a sequence of random blocks based on the IV and. Most modes require a unique binary sequence often called an initialization vector IV for each encryption operation.
This is the simplest mode whereby each block of data is simply encrypted with the same.
Block Cipher Modes Of Operation Learn 5 Important Modes Of Operations

Computer Network Block Cipher Modes Of Operation Tutorialspoint Dev

No comments for "How to Check Which Block Cipher Modes of Operation Used"
Post a Comment